Blog
November 25, 2015
Mutual authentication using Apache and a web client can be tricky. In this blog, we walk through the Apache client certificate authentication process and how to do it.
What Is Client Certificate Authentication?
Back to topClient certificate authentication refers to a certificate used to authenticate clients in SSL.
How to Do Apache Client Certificate Authentication
All that is taking place here beyond standard SSL is that the server will also authenticate the client that is requesting access.
1. Requirements for Authentication
First, some assumptions must be made to get this up and running. You will need to have the following:
| An Apache instance that has mod_ssl enabled. | Verification: run the following
apachectl –M | grep ssl You should see something like this: ssl_module (shared) If you don’t have this then you will need to get this enabled in order to continue. |
| Proper access. | To:
• Apache |
2. Generate the Certificate
Let's begin with the documented steps below:
| Generate the certificate for the self signed CA. | openssl req -newkey rsa:2048 -nodes -keyform PEM -keyout selfsigned-ca.key -x509 -days 3650 -outform PEM -out selfsigned-ca.crt
New items: |
| Create the SSL server's private key. | openssl genrsa -out selfsigned.key 2048
New items: |
| Create the Apache server CSR. | openssl req -new -key selfsigned.key -out selfsigned.csr
New items: |
| Sign the Apache server CSR. | openssl x509 -req -in selfsigned.csr -CA selfsigned-ca.crt -CAkey selfsigned-ca.key -set_serial 100 -days 365 -outform PEM -out selfsigned.crt
New items: |
3. Configure Apache
Now, looking at this from the Apache SSL point of view, what we have below is sufficient for one-way or standard SSL communications.
| Apache configuration | Place your certificate and key generated from above into the location below.
If you need to place it somewhere else, be sure to modify the path for the two SSL directives below. Either way, change those two directives in your httpd configuration in Path/to/apache/conf/extra/httpd-ssl.conf or in your vhost configuration if that is where you are enabling use of SSL. SSLCertificateFile "/etc/pki/tls/rselfsigned.crt” |
This is sufficient for one-way SSL communications.
Need Help?
Our open source experts are here to provide technical support and professional services.
4. Make Sure SSL Works
Let's check Apache and make sure SSL is working properly:
| Ensure that the SSL-enabled Apache instance works. | Verification: run the following
Openssl s_client –connect host.domain.com:443 You should see: CONNECTED And a bunch of other text and a BEGIN CERTIFICATE block. If you do, all is well. |
At this point SSL is functioning properly on the Apache web server.
5. Begin Mutual Authentication
In your SSL configuration file (the local selected above) add the following:
• SSLVerifyClient
• SSLVerifyDepth 10
• SSLCACertificateFile /path/to/cert/selfsigned-ca.crt
Once again, follow the documented steps below:
| Generate the client's private key. | openssl genrsa -out selfsigned-cli.key 2048
New items: |
| Create the client CSR. | openssl req -new -key selfsigned-cli.key -out selfsigned-cli.csr
New items: |
| Sign the client CSR. | openssl x509 -req -in selfsigned-cli.csr -CA selfsigned-ca.crt -CAkey selfsigned-ca.key -set_serial 101 -days 365 -outform PEM -out selfsigned-cli.crt
New items: |
| Bundle the client's certificate and client's key into a p12 pack. | openssl pkcs12 -export -inkey selfsigned-cli.key -in selfsigned-cli.crt -out selfsigned-cli.p12
New items: |
6. Test the Apache Certificate Authentication
Restart Apache with: apachectl restart.
Attempt to access it via https. You will be prevented from doing so without the client side certificate you just created because Apache is looking for it in the exchange.
Add the new certificate bundle (selfsigned-cli.p12) to your keychain on your workstation. Now, in your browser access the https URL once again. You will be challenged with something like this:
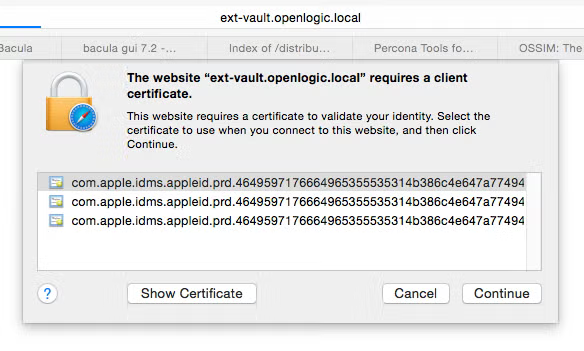
Since the certificate is on my keychain, I can simply select it from the list. (Above are three copies of the same not sure how that occurred, just ignore the others.)
After picking the certificate, VIOLA! I now have access via mutual authentication.
That is how to setup mutual authentication using Apache and a web client.
Back to topGo Beyond Apache Client Certificate Authentication
Authentication can be tricky, whether you're using Apache client certificates or microservices.
Authentication is especially important for security in microservices.
Get More Guidance
In our white paper, Wildfly for Microservices Authentication, learn:
- About your options for microservices authentication.
- When it can be advantageous to use Mutual TLS for client certificate authentication instead of TLS or JWT.
- A step-by-step tutorial for implementing Mutual TLS authentication.
- How to manage certificates with Wildfly Elytron Client SSL Contexts.